AWS S3 開啟 Public Access 讀取網頁
Posted On 2024年9月15日 星期日 at 於 晚上11:51 by Lani1. AWS 服務先選S3
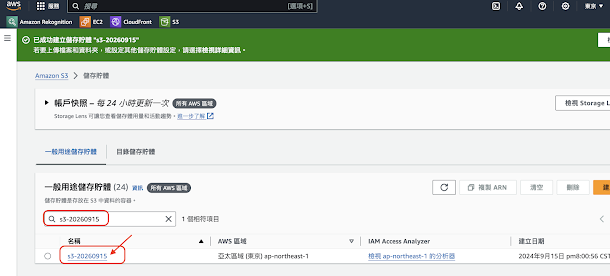
10. 點擊會以下網址出現 Access Denied
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PublicReadGetObject",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::s3-20260915/*"
} ]
}
紅框資源名稱要一致 , 將畫面拉到最下方儲存變更
使用者:arn:aws:iam::805158xxxxxx:user/xxx 無權對資源:「arn:aws:s3:::s3-20260915」執 行 s3:PutBucketPolicy,因為公共策略被 BlockPublicPolicy 阻止公共存取設定。
Sendmail check_*
Posted On 2012年10月5日 星期五 at 於 上午9:27 by Lani最近遇到一些Sendmail的問題,
認真的研究一下後,發現其實Sendmail也蠻多檢查機制。
Introduction
If you plan to upgrade your sendmail version, go directly to the current release of sendmail (or at least 8.9.3) which has standard FEATUREs included. However, you may read on, because this page and related pages give background informations about the check_* rulesets.
sendmail 8.8 introduced several new rulesets to control who can use your machine to send/relay e-mail and to avoid UBE from well known sites. These are:
- check_relay
- checking the host name and host address separated by $|. This ruleset is called whenever a client connects via (E)SMTP to the server.
- check_mail
- for the MAIL command.
- check_rcpt
- for the RCPT command (used to prevent unauthorized relaying). This ruleset disables all kinds of known relaying tricks (the trick which is tested by ORBS currently (1999-07-14) is fixed since the end of 1997 according to my logs).
- check_compat
- checking both MAIL and RCPT also separated by $| before delivery.
http://www.sendmail.org/~ca/email/check.html#check_rcpt
Google Search Stories TW
Posted On 2012年5月18日 星期五 at 於 中午12:33 by Lani在看上一篇 Proud of you blog 時,無意間被這影片所吸引。
第一個故事,雖然我早知道這小朋友的故事,但這是第一次看到完整版,蠻厲害的。
第二個故事,可能讓人有一些啟發,也蠻配服的。
分享給大家其他的 Google Search Stories TW
http://www.youtube.com/user/searchstoriestw
吳承儒:
高鐵上的小科學家
14歲的吳承儒,用 Google 搜尋老師的名字意外發現測量震動的方法,
一個月內坐了兩百趟高鐵,讓他成了2012年台灣國際科展最年輕的得獎者。
林容如:
打造職涯第一桶金
為了幫剛創業的公司尋找資金,透過 Google 搜尋,林容如找到了「千兆挑戰」商業企劃書競賽,並贏得職涯第一桶金,獲得了一個改變人生的機會。


























